Demystifying Azure RBAC: A Comprehensive Guide to Role-Based Access Control
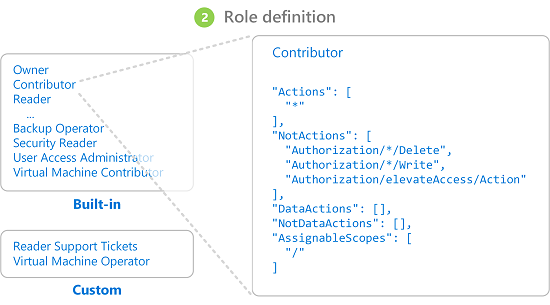
Let’s dive into the world of Role-Based Access Control (RBAC) and explore how it works in the context of Microsoft Azure. In this in-depth blog post, we’ll cover the key concepts, practical implementation, and benefits of Azure RBAC. What is Azure RBAC? Azure RBAC is a built-in authorization system that helps manage access to Azure resources. It allows you … Read more