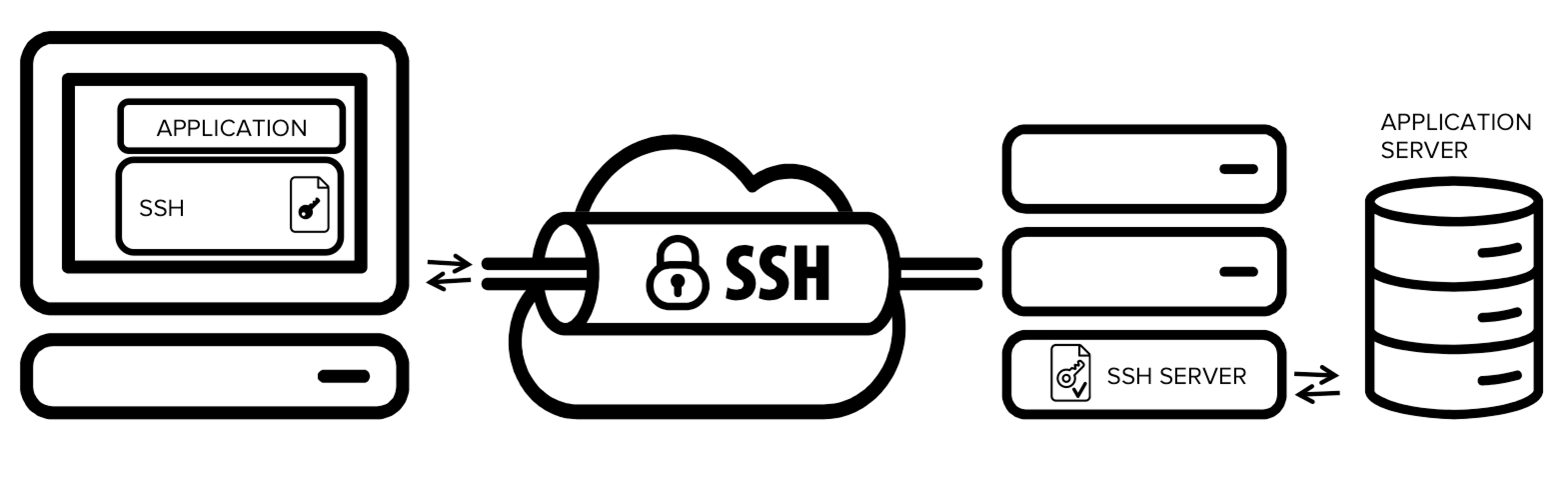
SSH tunnelling is a powerful technique that allows for the creation of secure communication channels between two hosts over an existing SSH connection. This method utilizes the authentication and encryption features inherent in SSH to ensure the confidentiality and integrity of data during transit. In this blog post, we’ll delve into the details of SSH tunnelling, exploring its types and practical applications.
Understanding SSH Tunneling
SSH tunnels leverage the robust authentication and encryption mechanisms of SSH, guaranteeing the security of data in transit. This is particularly crucial in scenarios where sensitive information needs to be transferred securely between hosts.
Types of SSH Tunneling
Local Port Forwarding (SSH Tunnel)
Local port forwarding is the most straightforward form of SSH tunnelling. It involves forwarding data from a port on the local machine to a port on a remote server. This type is commonly used for accessing services hosted on private networks.
ssh -L 1234:localhost:5678 remoteuser@remotehostIn this example, data arriving on port 1234 of your machine is encapsulated as SSH data and forwarded to port 5678 on remotehost.
Reverse SSH Tunnelling (Remote Port Forwarding):
Reverse SSH tunneling listens on a port of the remote machine and forwards data from that port to a specified port on your local machine via SSH. This is useful for scenarios where you want to access services on a remote machine as if they were local.
ssh -R 1234:localhost:5678 remoteuser@remotehostHere, data from port 1234 on the remote machine is sent to port 5678 on your local machine.
Dynamic SSH Tunnelling (Dynamic Port Forwarding):
Dynamic SSH tunnelling creates a dynamic SOCKS proxy, enabling the routing of traffic through an SSH connection. This is commonly employed for secure browsing or accessing intranet services across firewalls.
ssh -D 1337 remoteuser@remotehostThis creates the SOCKS5 proxy on port 1337 and can be used with curl as:
curl -x socks5://127.0.0.1:1337 <URL>Practical Examples
Accessing a Remote Service with cURL:
If you have a service running on a remote server and want to interact with it as if it were local, SSH tunneling and the curl command come in handy.
curl http://localhost:8080This command fetches data from the remote service via the SSH tunnel.
Securely Managing Remote Resources
SSH tunnelling provides a secure means of connecting to servers, databases, or other services without compromising security. It ensures that sensitive tasks, such as managing resources, can be performed seamlessly and securely without exposing the service directly.
Conclusion
In conclusion, SSH tunnelling is a versatile tool that enhances security and facilitates seamless communication across networks. By understanding its principles and practical applications, users can navigate the world of secure remote access confidently. Whether accessing services on private networks or managing remote resources securely, SSH tunnelling proves to be an invaluable skill in today’s interconnected digital landscape.