Let’s dive into the world of Role-Based Access Control (RBAC) and explore how it works in the context of Microsoft Azure. In this in-depth blog post, we’ll cover the key concepts, practical implementation, and benefits of Azure RBAC.
What is Azure RBAC?
Azure RBAC is a built-in authorization system that helps manage access to Azure resources. It allows you to define who can perform specific actions on your resources based on their roles within your organization. Here are some essential terms to get us started:
- Azure Subscription: A logical bundle of Azure resources, serving as a single billing unit. An account can have multiple subscriptions, but each subscription maps to only one account.
- Resource Providers: These provide the resources available within a subscription. They describe the applicable actions for each resource.
- Resource Group: A central unit for collecting related resources. It aids in provisioning, monitoring, and controlling resource members collectively.
Also Read: SSH tunnelling: A comprehensive guide for mastering Secure Shell
Key Concepts of RBAC
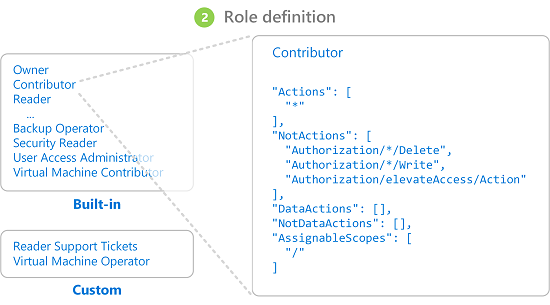
- Roles: Roles define a collection of permissions. Each role specifies the actions that can be performed, such as read, write, or delete. Azure provides built-in roles (e.g., Owner, Contributor, Virtual Machine Reader), but you can also create custom roles tailored to your organization’s needs.
- Security Principals:
- Users: Represent individuals with profiles in Azure Active Directory.
- Groups: Aggregate users for easier management.
- Service Principals: Represent identities used by applications or services to access resources.
- Managed Identities: Allow resources to authenticate themselves without explicit credentials.
- Scope:
- Scopes define the set of resources to which access applies. You can specify scope at different levels:
- Management Group: Organize subscriptions hierarchically.
- Subscription: A logical bundle of resources.
- Resource Group: Collect related resources.
- Individual Resource: Fine-grained control for a specific resource.
- Scopes define the set of resources to which access applies. You can specify scope at different levels:
Practical Implementation of RBAC
- Assigning Roles:
- Use the Azure portal, Azure CLI, or PowerShell to assign roles to users, groups, or service principals.
- Roles include:
- Owner: Full control over resources.
- Contributor: Can manage resources but not assign permissions.
- Reader: View-only access.
- Many more specific roles for different tasks.
- Effective Permissions:
- Understand how roles cascade from higher scopes to lower ones.
- For example, a role assigned at the subscription level applies to all resources within that subscription.
- Auditing and Monitoring:
- Regularly review role assignments and audit logs.
- Ensure that permissions align with organizational policies.
How Azure RBAC determines if a user has access to a resource
The following are the high-level steps that Azure RBAC uses to determine if you have access to a resource. These steps apply to Azure Resource Manager or data plane services integrated with Azure RBAC. This is helpful to understand if you’re trying to troubleshoot an access issue.
- A user (or service principal) acquires a token for Azure Resource Manager. The token includes the user’s group memberships (including transitive group memberships).
- The user makes a REST API call to Azure Resource Manager with the token attached.
- Azure Resource Manager retrieves all the role assignments and deny assignments that apply to the resource upon which the action is being taken.
- If a deny assignment applies, access is blocked. Otherwise, the evaluation continues.
- Azure Resource Manager narrows the role assignments that apply to this user or their group and determines what roles the user has for this resource.
- Azure Resource Manager determines if the action in the API call is included in the roles the user has for this resource. If the roles include
Actionsthat have a wildcard (*), the effective permissions are computed by subtracting theNotActionsfrom the allowedActions. Similarly, the same subtraction is done for any data actions.Actions - NotActions = Effective management permissionsDataActions - NotDataActions = Effective data permissions - If the user doesn’t have a role in the action at the requested scope, access isn’t allowed. Otherwise, any conditions are evaluated.
- If the role assignment includes conditions, they’re evaluated. Otherwise, access is allowed.
- If conditions are met, access is allowed. Otherwise, access isn’t allowed.
Where is Azure RBAC data stored?
Role definitions, role assignments, and deny assignments are stored globally to ensure that you have access to your resources regardless of the region you created the resource.
When a role assignment or any other Azure RBAC data is deleted, the data is globally deleted. Principals that had access to a resource via Azure RBAC data will lose their access.
Why is Azure RBAC data global?
Azure RBAC data is global to ensure that customers can timely access resources regardless from where they’re accessing. Azure RBAC is enforced by Azure Resource Manager, which has a global endpoint and requests are routed to the nearest region for speed and resilience. Therefore, Azure RBAC must be enforced in all regions and the data is replicated to all regions.
Consider the following example. Arina creates a virtual machine in East Asia. Bob, who is a member of Arina’s team, works in the United States. Bob needs to access the virtual machine that was created in East Asia. To grant Bob timely access to the virtual machine, Azure needs to globally replicate the role assignment that grants Bob access to the virtual machine from anywhere Bob is.
Final Thoughts
Azure RBAC empowers you to manage access with precision, ensuring that the right people have the right level of control over your Azure resources. By understanding RBAC concepts and implementing them effectively, you can enhance security while maintaining efficiency.